Circumstances in Which You Need to Use Secondary Files
Many student research projects involve secondary analysis of data that belongs to or was initially collected by their faculty advisor or another investigator. In addition because credit reporting companies use Social Security numbers and other personal information to identify a persons credit file using a new number doesnt guarantee a fresh start.
Finally the Bcc field Blind Carbon Copy is used when you want other people to receive the message but you dont want the other recipients to know they got it.

. But by being careful with your personal information and monitoring credit reports for fraudulent activity you can limit the misuse. Medicares secondary payment will be based on the full payment amount before the reduction for failure to file a proper claim unless the provider physician or other. Citizenship you can file for a citizenship certificate by filling out and submitting Form N-600 to USCIS and paying the filing fee.
Secondary school teachers in the state of Melaka Malaysia. Of the disclosing CE or the recipient CE when the appropriate relationship exists. 1 primary sources or 2 secondary sources.
You need to keep track of all the cases your firm has handled. Answers 2 and 3. Open existing document make changes Save make more changes Save Print Close.
Also you want to keep your files separated between operating systems to be sure that while an operating system is running it does not mess with the others operating system files. You are unable to work due to a non-work-related illness injury or pregnancy. In particular some utilities that are normally applied to ordinary files can be applied as well to some special files.
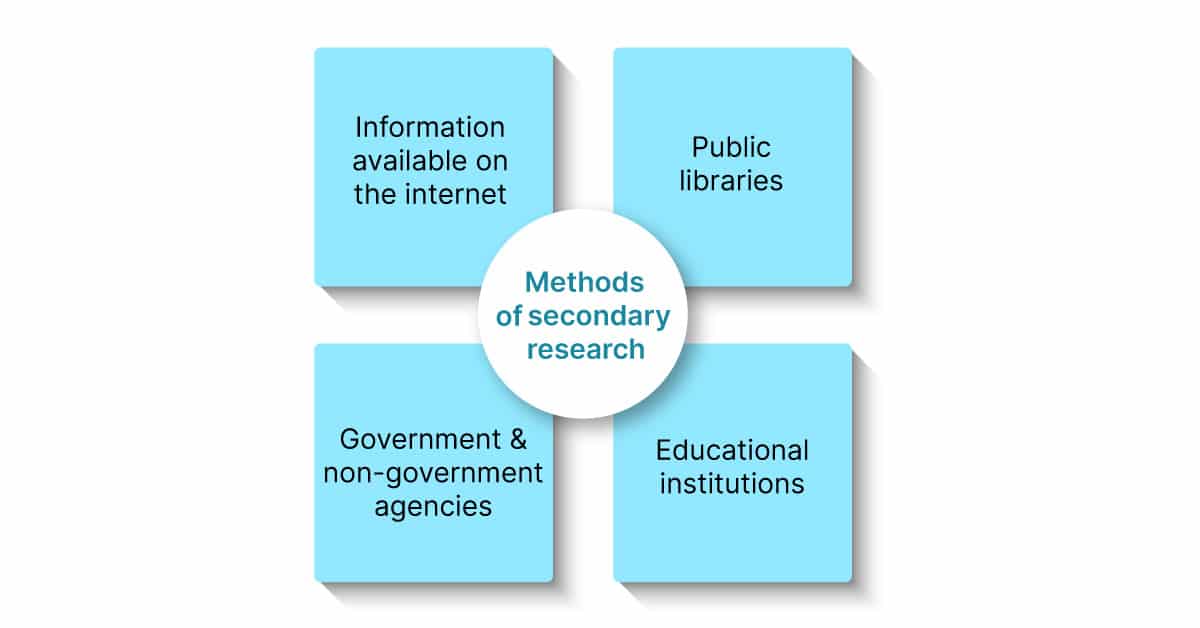
You can also make formatting changes to the entire presentation by only changing the top master slide 2. Secondary data refer to research information collected as a result of studies and similar efforts that can then be used by others either as comparison data or as part of new research. You can use this opportunity to demonstrate youve grown both academically and personally since you got that shaky GPA or suspension and admissions boards will appreciate your honesty.
645 The Defence Force as defined in s 61 may use or disclose personal information for a secondary purpose where it reasonably believes that the use or disclosure is necessary for a warlike operation peacekeeping civil aid humanitarian assistance a medical emergency a civil emergency or disaster relief occurring outside Australia and the external Territories s. The static assets like jpg png and pdf files are stored in S3 for cost efficiency and high durability. One of the exemptions listed to HPPs 101 and 111.
In the same vein Komba and Kira 2013 note that during teaching practice student teachers observe subject teachers at work so as to learn about teachers skills. The circumstances in which CEs are permitted but not required to use and disclose PHI for certain activities. Having two or more partitions on your computer is mandatory in this situation because each operating system needs a separate partition of its own.
For the purposes of this section well include both of these types of data in our discussion and not distinguish between them. Other laws may apply. Template for each type of slide that youll need in the presentation.
Use Save As when you want to create a new document. See In-Network and Out-of-Network CareBut you may need to go out of network for certain types of care especially if you or a member of your family has a rare illness such as a genetic disorder. If the student is provided with a de- identified non-coded data set the use of the data does not constitute research with human subjects because there is no interaction with any individual and no identifiable private.
Save replaces the original file. Receiving care from a provider in your health plans network usually costs you much less than going to an out-of-network provider. Treatment and for health care operations.
If you believe that you have already acquired or derived US. Secondary storage is needed to keep programs and data long term. Of course youll also need to prove your eligibility by submitting supporting documents as described in USCISs instructions for this form found.
Primary vs Secondary sources Before you can begin to conduct any form of academic work you need to consider whether it is appropriate to use. When people get an e-mail theyll see all the people in the To and Cc lines - but not Bcc. That is in some ways you can treat the device as a file.
When to use Bcc. Sources of archival data. Evidence has been collected through distribution of a modified adopted survey questionnaire.
Most applications provide space of around 500 words for you to provide any additional information you may wish to add to your application. A typical editing session for a given document might look like this. WHAT YOU NEED TO DO.
The division between primary and secondary sources is not always apparent but the differences discussed below are important. Secondary storage is non-volatile long-term storage. N use or disclosure for a directly related purpose which would be reasonably expected by the individual see Section 11 2 1 n use or disclosure to which the individual has consented see Section 11 2 2.
As these files are critical to your business you want to keep track of whats happening in your S3 bucket. Due to the fact that the appellate panel will be focusing heavily on the legal arguments that are being made in an appellate brief a paralegal who is drafting an appellate brief for their supervising attorneys review does not need to be concerned about using proper grammar. You will need to indicate how you want your claim to be processed by.
Overall the key issues and challenges found to be significant in using ICT tools by teachers were. Use Save when youre editing an existing document and you want to preserve your changes to it as you work. Without secondary storage all.
If you look up a definition of evidence you will find many variations but they all basically say evidence. If You Have Acquired or Derived US. You are unable to perform your normal work duties because you are sick or quarantined due to COVID-19.
Without first obtainingan individuals authorization. From campus-based learning as they are called upon to respond to new circumstances. One good use of Bcc is when sending an e-mail to hundreds of people.
You paid into the State Disability Insurance program noted as CASDI on paystubs via taxes. The table on page 2 describes the information and evidence you need to submit based on whether you wish to have your claim considered in the FDC Program Optional Expedited Process or in the Standard Claim Process. For example when you are accessing a Unix system using a mouse type the following command cat devmouse and then move the mouse.
You can still access the other tabs like the Home tab allowing you to adjust fonts and colors. Failed to file a proper claim the provider physician or other supplier must include this information on the claim for secondary payment that is submitted to Medicare. Is information given to the court and the jury to help them decide if a crime has been committed or not tends to prove the truth or probability of truth.
The secondary purposes listed under HPPs 10 and 11 are.

Engineers Files Second Cut Faithfulltools Com
Secondary Research Guide Uncover Secondary Research With Voxco Voxco

No comments for "Circumstances in Which You Need to Use Secondary Files"
Post a Comment